The password protection in Windows is a good precaution against nosy individuals. But really it is not that safe. If someone really want to get access to a password protected Windows computer – they probably will. There are software out there to help you do this, but with the right methods you don’t event need tools. In this tutorial we are going to have a look at how to hack a Windows 7 password for a local administrator account without using any tools at all.
We have a Windows 7 computer, which we cannot log in to because we do not have the correct password. The object is to remove the password and gain access.
1. Reboot the computer
Wait for the splash screen showing Starting Window is shown.
2. While the splash screen is shown, cut the power to the computer
3. Plug in the power in again and start the computer again
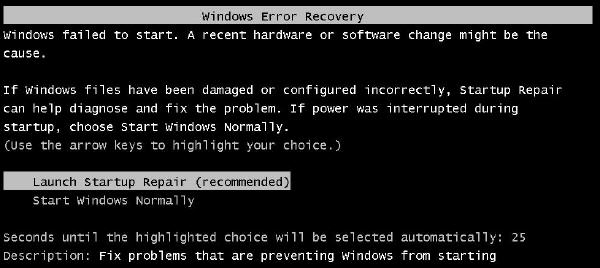
You will now get a screen asking you if you want to Launch Startup Repair (recommended)
4. Press Enter
Startup repair starts scanning the computer for problems, in the process the dialog box Startup Repair opens and asked if you want to restore form an earlier point in time.
5. Press the Cancel Button
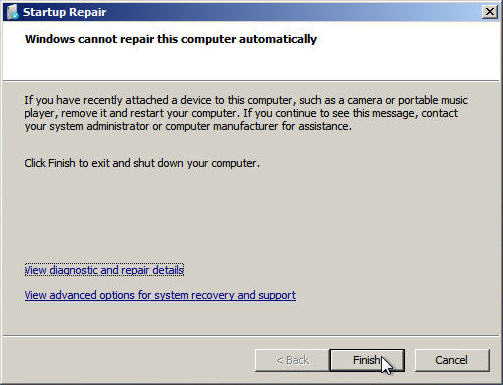
Let the scan finish, it might take a while to do so. Ones it’s done a new dialog box called Startup Repair appears to tell you that it was not able to repair the computer automatically.
6. Click the arrow next to View problem details
7. Scroll down to the bottom of the description box
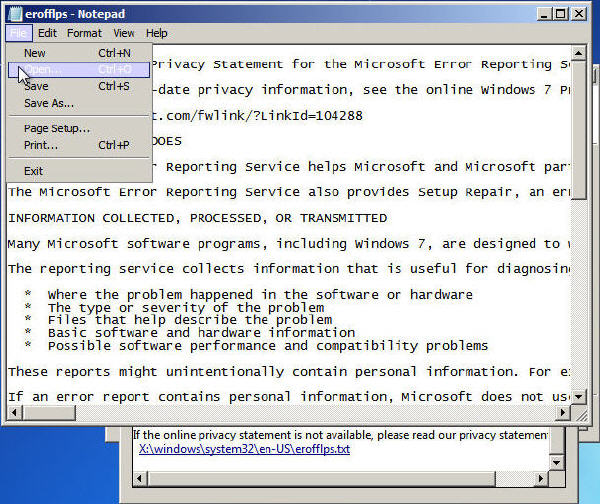
8. Click the link X:\Windows\System32\en-US\erofflps.txt
Notepad opens – and here comes the magic. You are now able to browse the system files with administrative rights. We will now make it possible to open an administrative command prompt from the login screen. We will do this with a small hack to the Sethc application, that is normally used to enable the Sticky Keys function by pressing the shift key five times.
9. Press File | Open
The dialog box Open opens
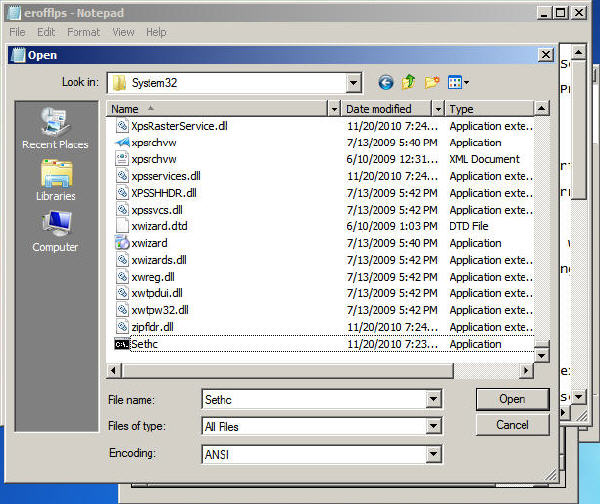
10. Browse to C:\Windows\System32
11. Choose All Files in the dropdown menu Files of Type:
12. Locate the file Sethc and rename it to Sethc1
13. Locate the file cmd and copy it
14. Renamed the copied file cmd – copy to Sethc
That’s it – We should now be able to press the Shift key five time and instead of opening the original Sethc application file, the OS will now open application cmd renamed to Sethc.
15. Close the dialog box Open and the text document erofflps.txt
16. Press the Don´t send button in the Startup Repair box
17. Click the Finish button
The computer is now shut down, turn it back on and wait for it to get to the login screen.
18. Press the Shift key five times
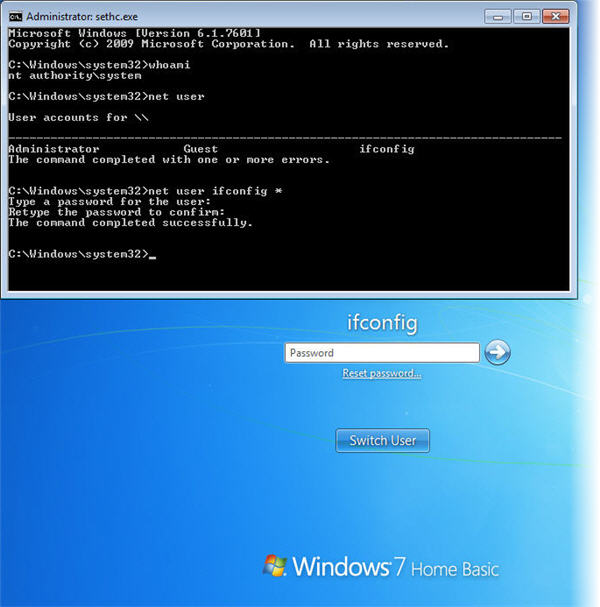
A command prompt opens. Let’s see who are logged in as.
19. Type whoami in the command prompt and press Enter
The command prompt returns the answer NT AUTHORITY\SYSTEM. This means that we are logged in as a local system account with highest level privileges. It is often used to run different background services on a Windows computer. Now let’s use this to remove the password of the user ifconfig.
20. Type net user and press Enter to see the accounts on this computer
In this tutorial the only account on the computer is ifconfig
21. Type net user ifconfig * and press Enter
22. You can now enter a new password – here we just leave it blank
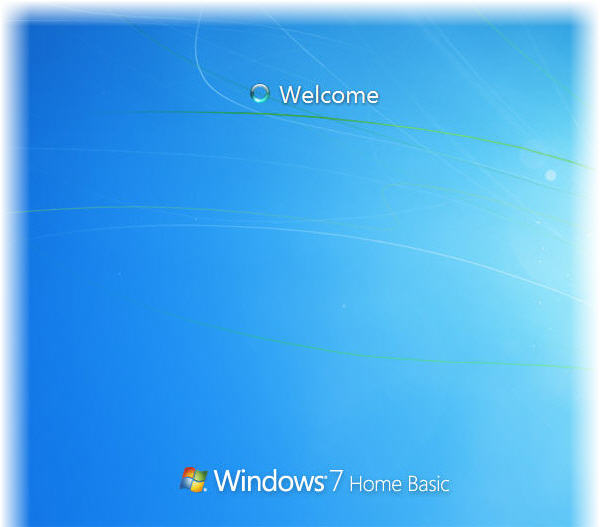
24. Login as the user ifconfig without a password
We can now see that the login was successful. The method should work on Windows 8 as well. This tutorial serves to prove that if you store sensitive information on you Windows computer, you should not rely on the Standard Windows password protection alone. Credit for the method goes Here








Nifty!
It looks like the source video was removed from Youtube. Sadface. Anyway, thanks for sharing this tip. Very handy!
After pressing the shift key five times and nothing will happen. Eventually I removed my forgotten Windows 8 admin password with PCUnlocker Live CD.
It worked when I made the tutorial, can’t say if MS has rolled out an update to fix the issue or something.
Thanks, it worked great for me, only I am limited to user actions and not any admin. thanks again
I went about it in a different way and used a live Linux distro to mv sethc.exe cmd.exe
This method is much more reliable because I was lucky that BIOS was not password locked and could USB boot.
Nice.